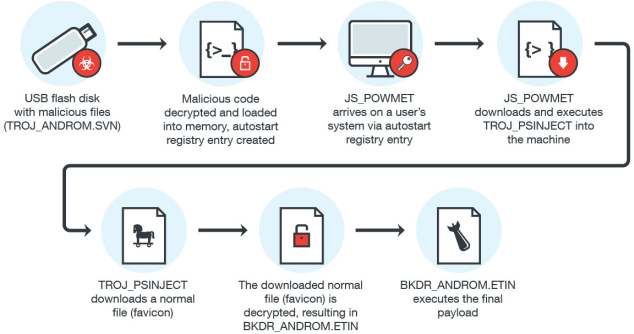
Amazon.com: Data Blocker USB - USB Blocker,100% Guaranteed Prevent Hacker Attack.Any Other USB Device Charging,USB-Data Blocker.Data Blockers for Apple Products (5 Red) : Electronics

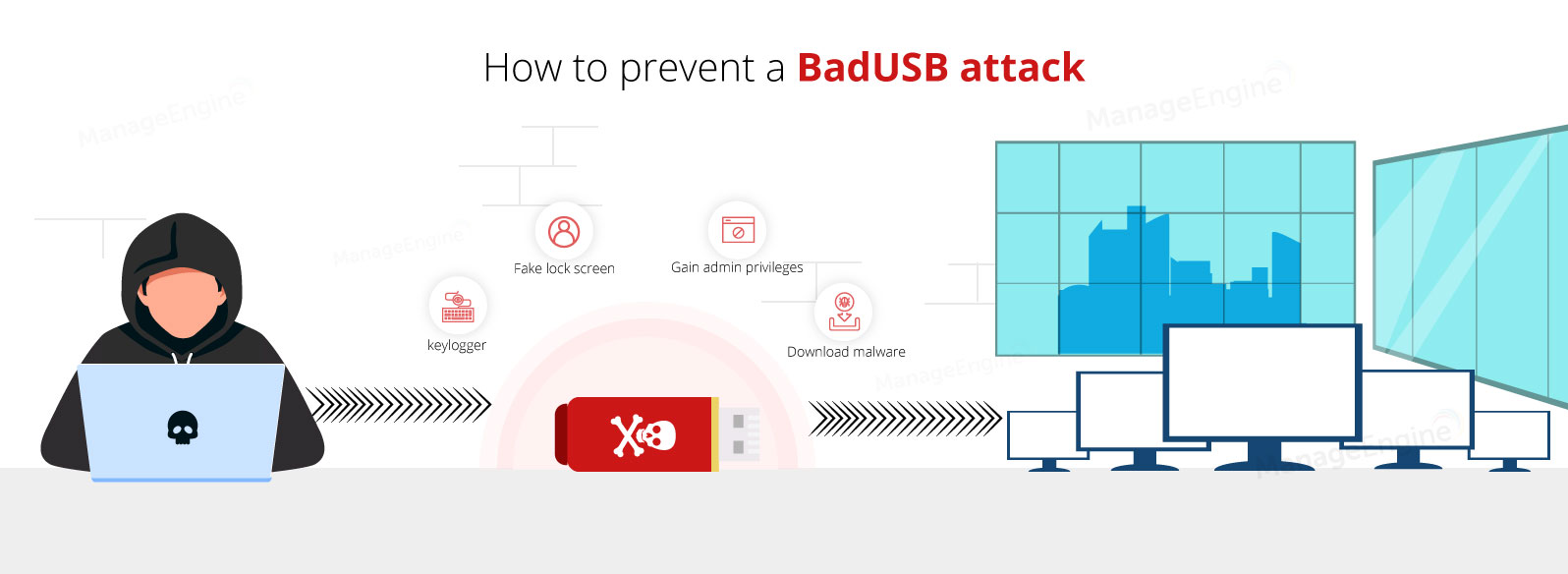
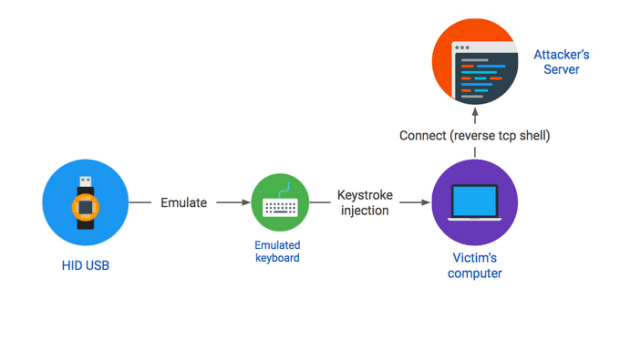
attacks - What are the risks and effects of the feared "Killer USB stick"? - Information Security Stack Exchange
Bow to the USBsamurai: Malicious USB cable leaves air-gapped networks open to attack | The Daily Swig