Electronics | Free Full-Text | New RSA Encryption Mechanism Using One-Time Encryption Keys and Unpredictable Bio-Signal for Wireless Communication Devices

Enhanced key-generation algorithm using MRMCTT in Data encryption standard algorithm | Semantic Scholar
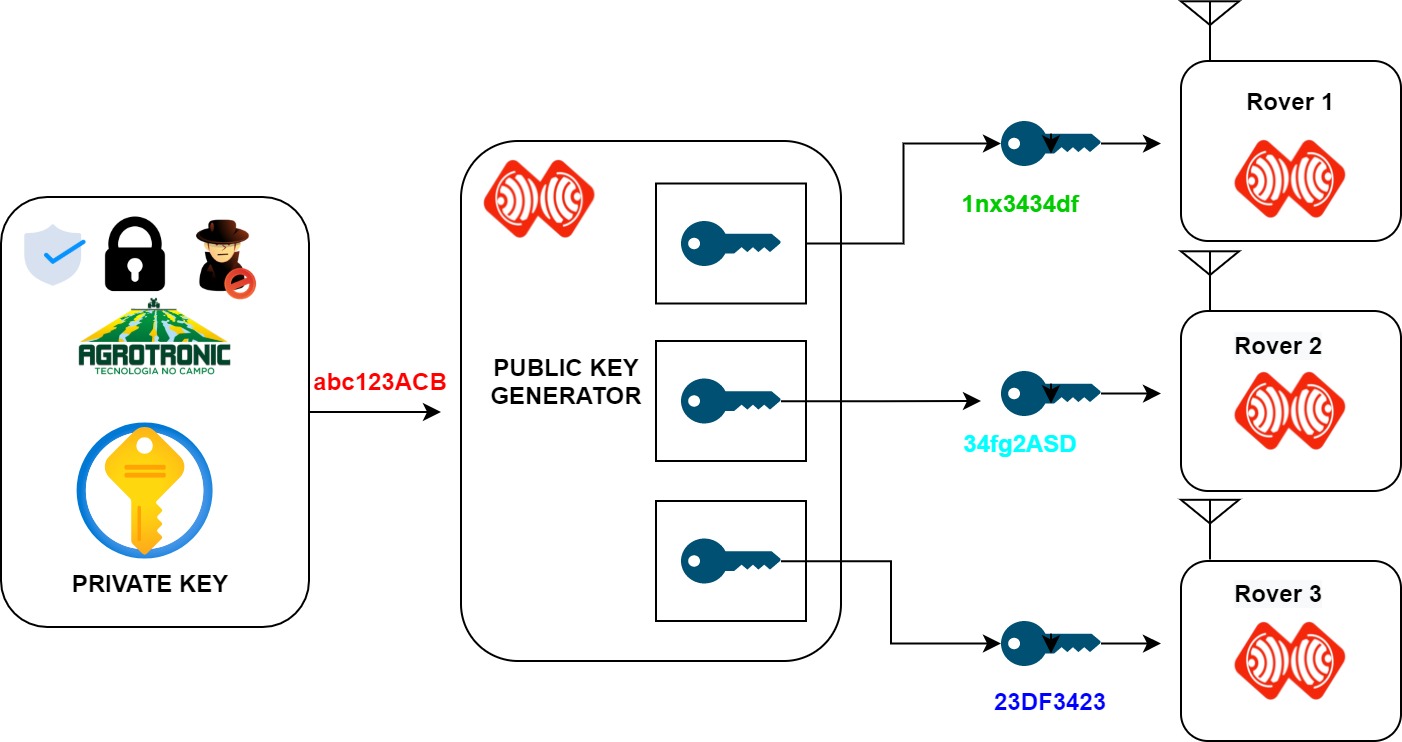


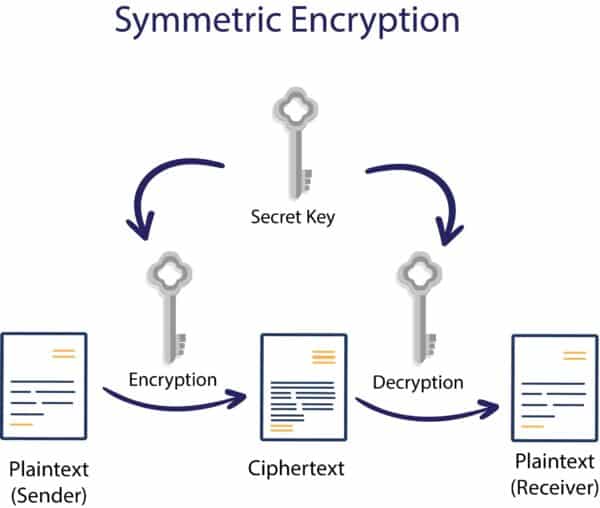



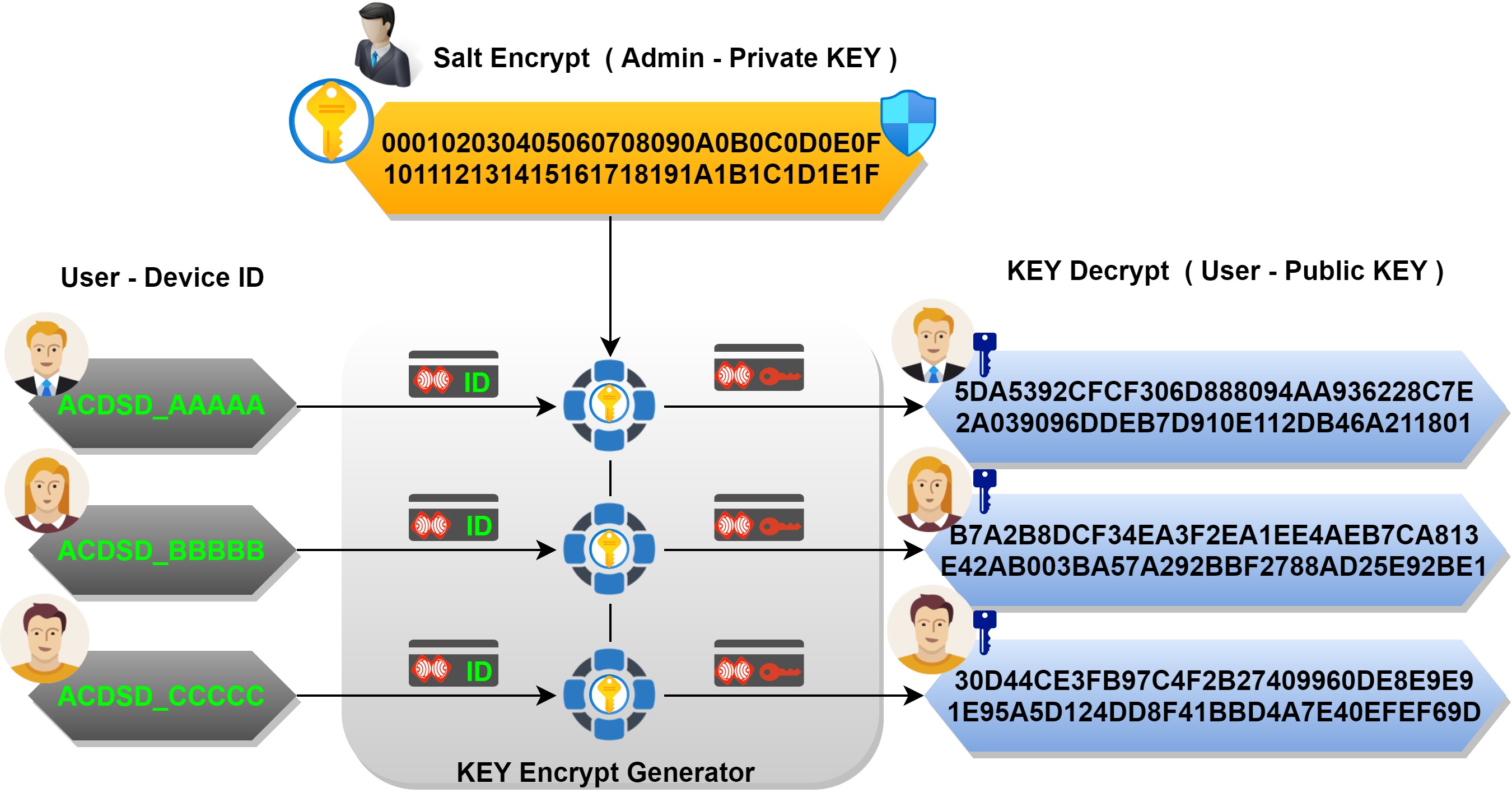


![MS-DRMND]: Content Encryption for AES in Counter Mode | Microsoft Learn MS-DRMND]: Content Encryption for AES in Counter Mode | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-drmnd/ms-drmnd_files/image007.png)