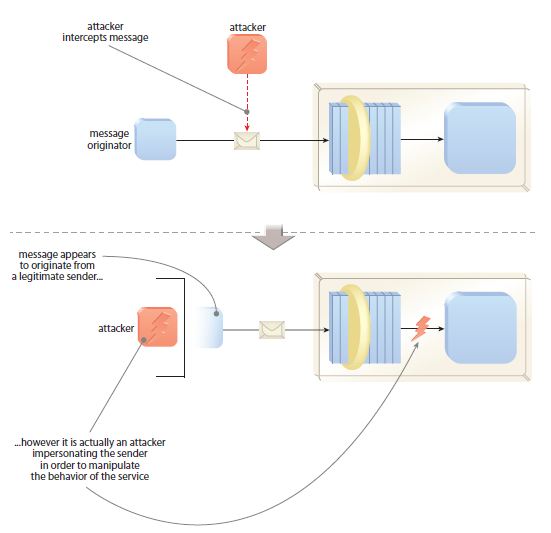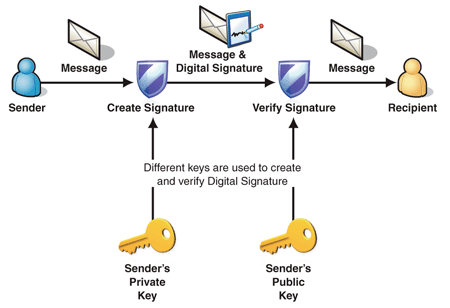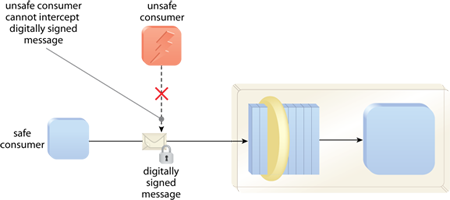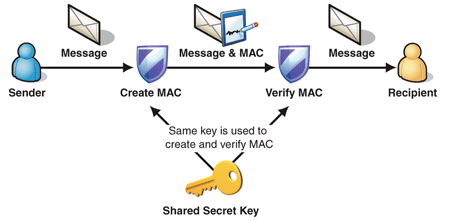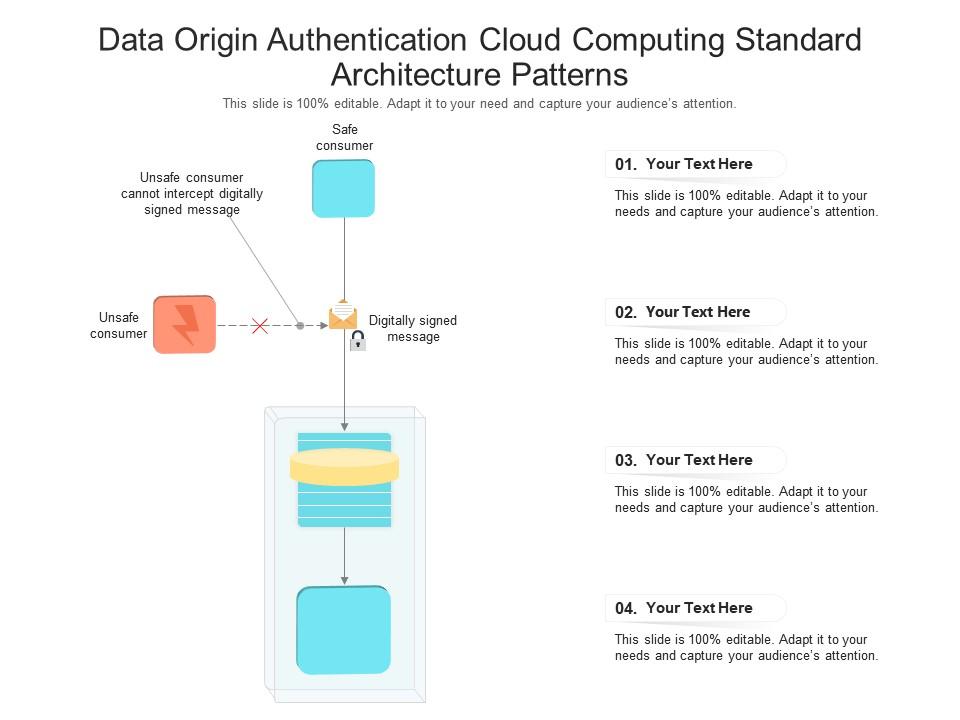
Data Origin Authentication Cloud Computing Standard Architecture Patterns Ppt Presentation Diagram | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Data Origin Authentication Cloud Computing Standard Architecture Patterns Ppt Presentation Diagram | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

CryptographyBhutan - Lesson 12 #securitymechanism #securityservices Security services are implemented by a security mechanism or combination of mechanisms: 1. Peer entity authentication service can be implemented by or combination of Encipherment, Digital